Understanding the power of EMM
“Information technology and businesses are becoming inextricably interwoven. I don’t think anybody can talk meaningfully about one without talking about the other" - Bill Gates
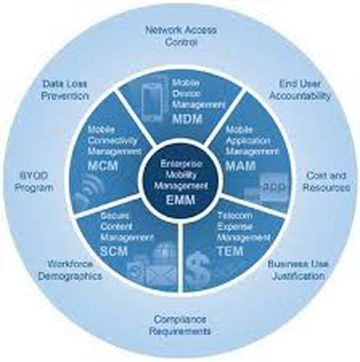
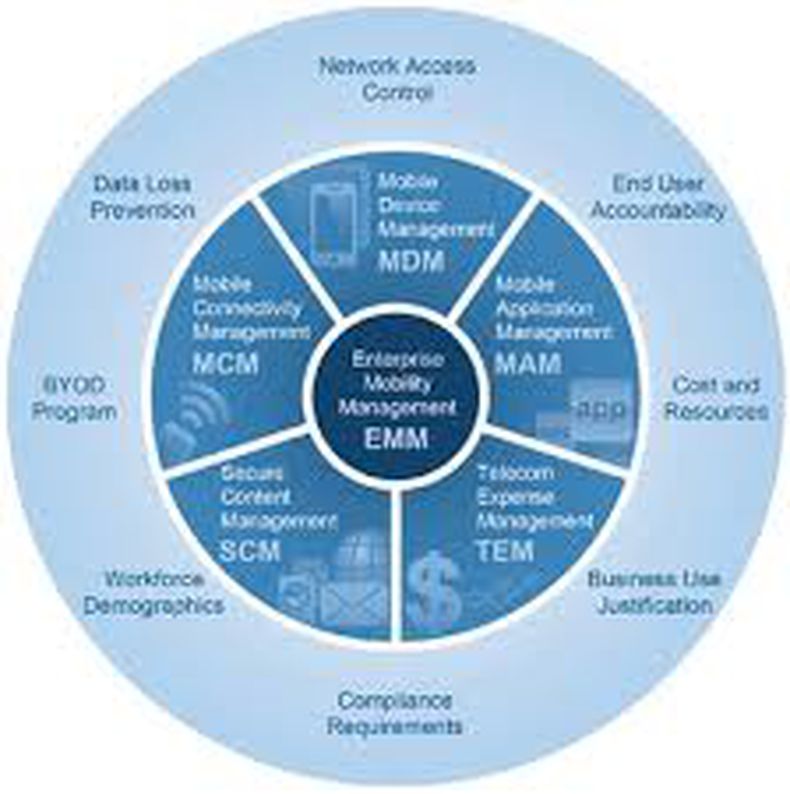
Enterprise Mobility Management (EMM) is the set of people, processes and technology focused on managing mobile devices, wireless networks and mobile computing services in a business context. As more working professionals have smart phones and tablets, EMM has become increasingly significant.
The goal of EMM
- Is to determine if and how mobile information technology should be integrated with work processes and objectives
- Is to support the staff when they are using these devices at the workplace
Management alone does not make a successful mobile enterprise strategy. Businesses need to help workers with apps and access to corporate data. EMM typically involves some combination of mobile device management (MDM), mobile application management (MAM) and mobile content management (MCM), Bring your own device (BYOD). It is up to the enterprise to evaluate solutions to choose out of this.
Mobile Data Management (MDM) lets IT administrators enforce:
- Passcode requirements.
- Track the location of devices.
- Remote wipe lost/stolen devices.
All these are done to protect corporate data. They don’t solve data security threats. With MDM alone, for example, there is no way to stop an employee from uploading data to an unsecure cloud service so that he can access it on his PC at home. MDM has lot of control structures. MDM controls the full device, for example wiping a lost phone to prevent the company’s financials from falling into wrong hands also deletes the personal data of the user.
Mobile Application Management (MAM) and Mobile Content Management (MCM) are some of the areas of EMM (Enterprise Mobility Management). They give EMM more granular control solely over corporate assets. Administrators can enforce policies on specific apps and pieces of data. The inclusion of these technologies has opened the door for EMM products to include features that enable mobile workers, such as enterprise app stores, managed email and productivity apps, and secure file sharing and synchronization.
Security is a crucial part for any technology implementation. Because mobile devices are easily lost/stolen, data on these devices become vulnerable. EMM is a set of systems intended to prevent unauthorized access to enterprise application and/or corporate data on mobile devices.
The security policies are centrally managed and enforced and they are programmed to support and cooperate with the application programming interfaces (APIs) from various device makers to increase security compliance. The data transfer between mobile device and the enterprise should be encrypted. This can be done through VPN (Virtual Private Network) tunnel or over HTTPS (Hypertext Transfer Protocol Secure) with two-factor authentication.
Mobile devices in companies with “bring your own device” (BYOD) policies are often used both personally and professionally. In these cases corporate IT has less control over the device and damage can be caused to the corporate data. Data storage on the mobile device should be limited and centrally organized with relevant policies.
EMM helps
- Mobilize employees on their terms.
- Maximize customer experience.
- Create value.